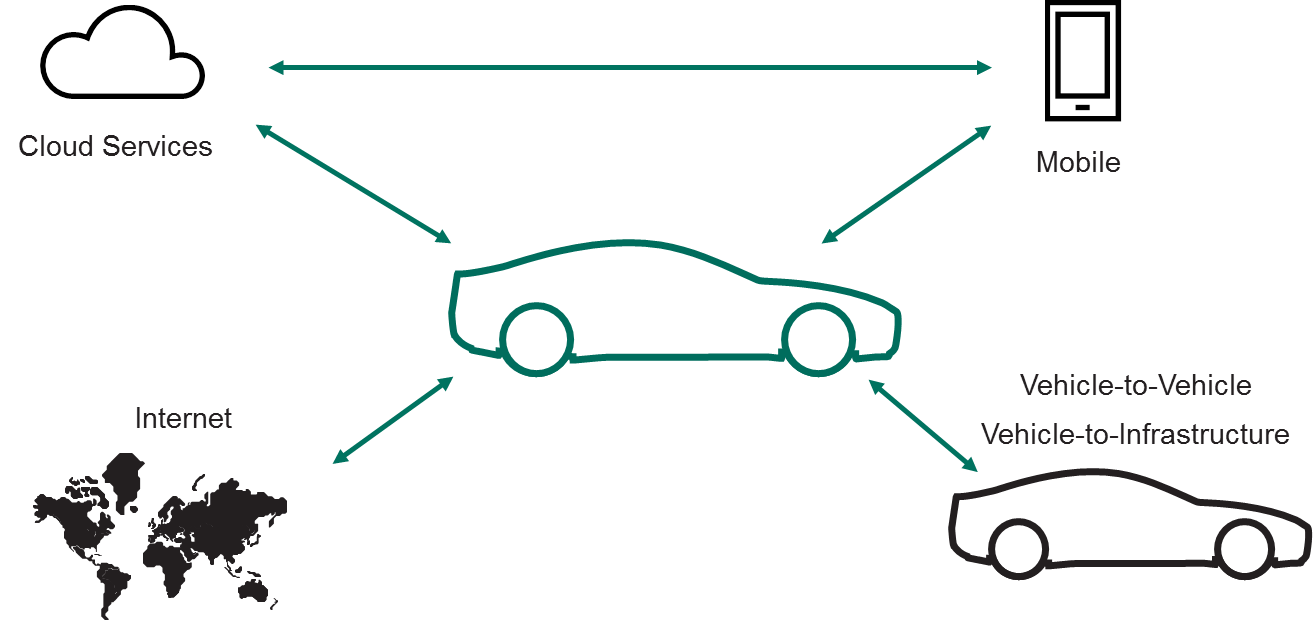
A Proper Approach To Cybersecurty Of Cars Kaspersky Official Blog
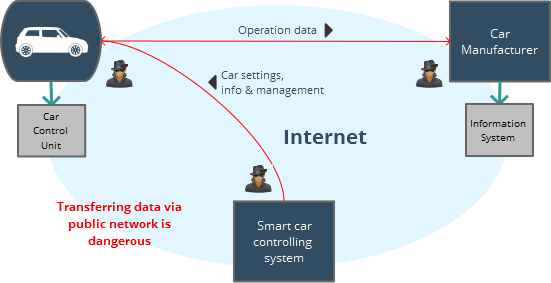
Security Is Driving The Adoption Of Connected Cars Teskalabs Blog

Fooling Detection Alone Is Not Enough First Adversarial Attack Against Multiple Object Tracking

Fooling Detection Alone Is Not Enough First Adversarial Attack Against Multiple Object Tracking

Thief Car Free Vectors Stock Photos Psd

Approach For An Automotive Vulnerability Database Download Scientific Diagram

Fooling Detection Alone Is Not Enough First Adversarial Attack Against Multiple Object Tracking
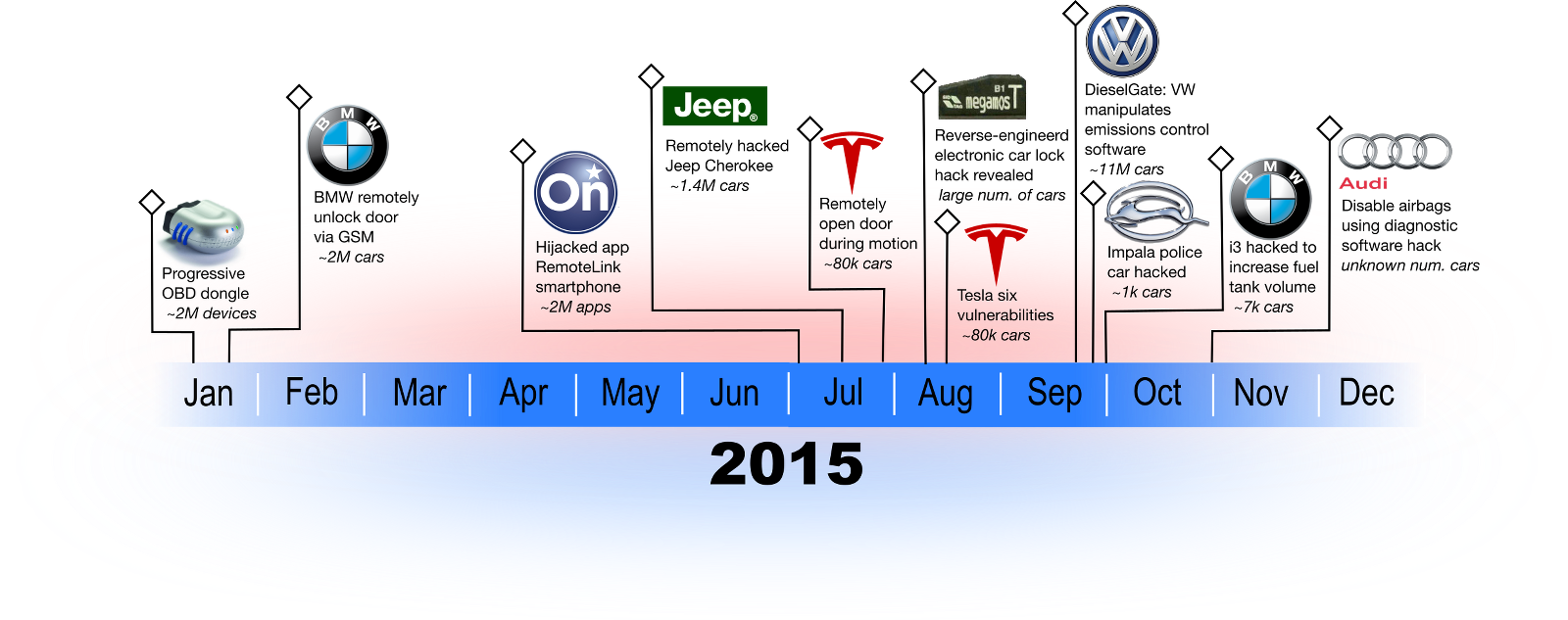
2015 Automotive Security Panorama Arminw
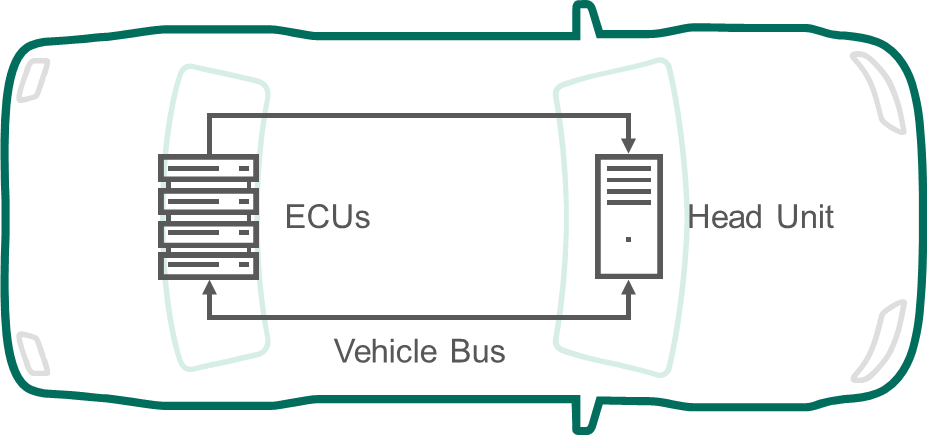
A Proper Approach To Cybersecurty Of Cars Kaspersky Official Blog

Carrier Level Immutable Protection Clip Secure And Trusted Technology To Empowering Carriers Think Big

Cybersecurity Industry Report Investment Case Nasdaq
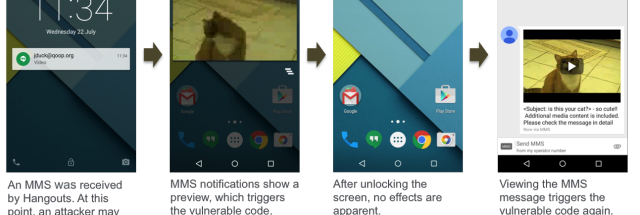
950 Million Android Phones Can Be Hijacked By Malicious Text Messages Ars Technica

Threat Intelligence Archives Sonicwall

Threat Intelligence Archives Sonicwall

Fooling Detection Alone Is Not Enough First Adversarial Attack Against Multiple Object Tracking Deepai
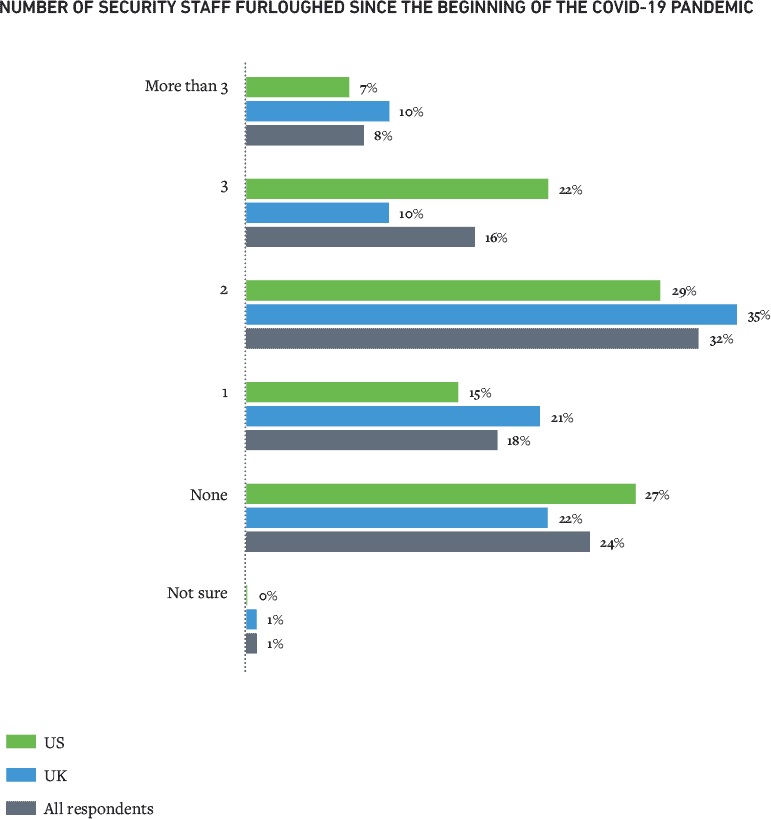
Passwords Stronger Security

When Toasters Attack Ipro
Malvertising Wikipedia
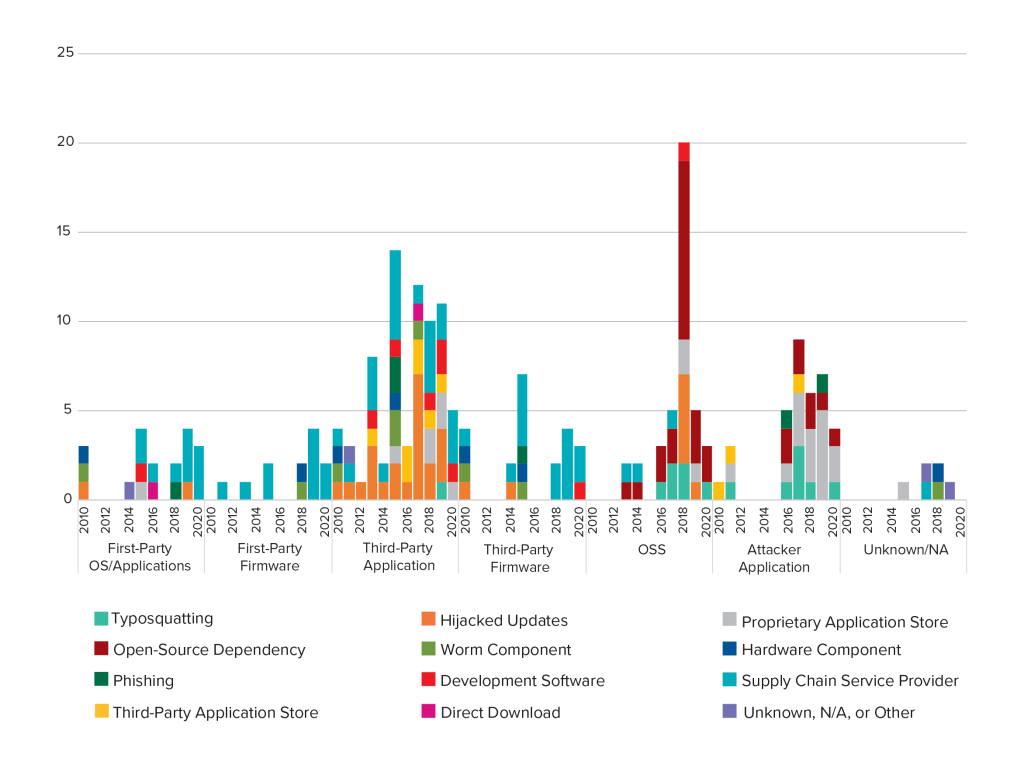
Breaking Trust Shades Of Crisis Across An Insecure Software Supply Chain Atlantic Council
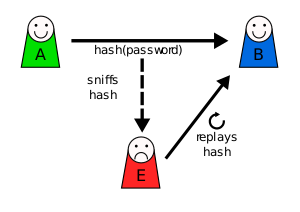
Replay Attack Wikipedia